Cyberattack vs. data breach: what’s the difference?
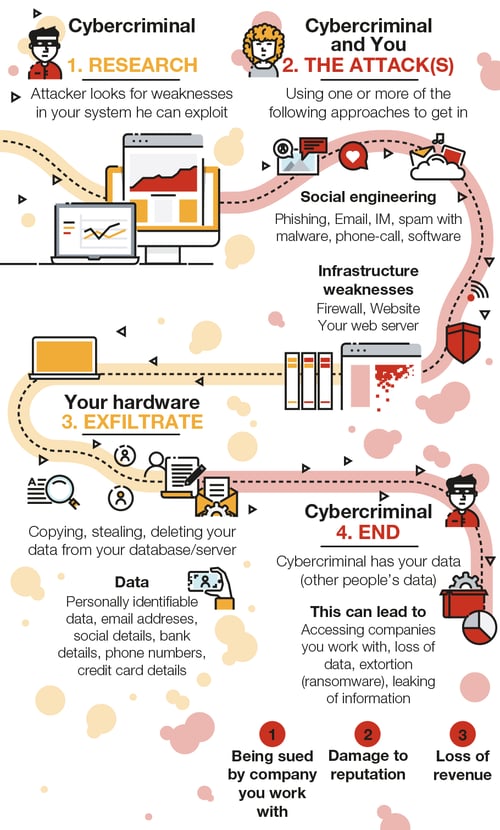
A cyberattack is simply a digital attack on computer systems, networks, devices, and/or applications. The objective is usually to disable computer systems or steal data. Attackers can use a variety of tools and techniques to achieve their goals, including phishing emails, ransomware, viruses, and denial-of-service attacks. A data breach is one potential consequence of a successful cyberattack. The types of data they are looking for could be passwords, email addresses, personal information, or financial information.
Threats
The following statistics paint a vivid picture of the threats to SMB data:
52% of small businesses experienced cybersecurity breaches in the past year.
Cybersecurity breaches cost UK businesses approximately £30 billion in 2016.
60% of small firms don’t know the source of the most disruptive cybersecurity breach or attack in the last twelve months.
Across the globe, just under 5 million records a day are compromised through a data breach.
On average, it takes 120 days for a business to discover a data breach.
In summary, data breaches are common, often go undetected at first, and can cost businesses – who don’t know how to protect themselves - thousands.
What is a data breach?
What can SMBs do to protect themselves?
Putting a cost-effective cybersecurity strategy in place can help to better protect you further down the line.
Strategy Step 1: Understand the elements of proper data protection
The first step in creating a cybersecurity strategy is to truly understand what is meant by ‘data protection’. Think of it in terms of the CIA acronym:
Confidentiality
Integrity
Availability.
This means your data needs to be kept confidential. It should only be available to people with relevant privileges. Your data should maintain its integrity and be in the format the user requires it to be (and not to have been materially altered by the system capturing, storing, or transmitting it.) Finally, your data should be available whenever the person with those relevant privileges is requesting it.
Strategy Step 2: Assess
The first step in assessing your customers’ potential vulnerabilities is to identify all the physical and virtual computing devices within the organization. Together with your client, make a list that includes all of them:
• Workstations and laptops• Network file servers• Network application servers• Corporate firewalls and switches• Multi-function printers• Mobile devices.
This infrastructure assessment should distinguish between cloud and on-premise systems and devices. This makes it easier for you to determine all possible storage locations for data. The number one threat to devices is a hybrid ransomware attack. For people, it’s targeted social engineering.
Now, categorize all business data and divide it into three locations: cloud,on-premise systems, and devices. For example:
• Cloud On-premise systems Devices• Cloud email and applications• Cloud storage• Websites and social media• Databases• Company-wide file sharing and storage• Intellectual property• Presentations• Company memos• Statistics and reports.
Read our white paper on the three essential components of managed security services.
Strategy Step 3: Identify relevant security measures
Once you’ve assessed what data is important to your business, where it resides, and who has access to it, you can determine the relevant security measures you should adopt. These may include:
Purchasing tools (for example, AVG antivirus Subscription for small businesses).
Redesigning your security protocols.
A wholesale change in your business’s attitude towards data security.
Training for all members of staff.
Data protection must be discussed and supported at every level within your business. It is as critical for senior executives as it is for junior team members, all of whom will have access to sensitive data of some kind. Take the time to review what data they may handle, and put the relevant measures in place.
Steps for protecting data
There are plenty of good security measures all businesses can apply today that will help prevent or reduce the chances of data loss, breach, or theft. These tools and solutions come in many shapes and sizes, but all have a role to play in protecting your sensitive and private data.
1: The basics
Install firewalls
Install AVG antivirus Subscription
Install encryption software.
2: Staff awareness
Use strong passwords.
Consistently communicate the importance of staff caution when clicking on links or attachments.
Provide training and education for staff on how to be security-aware.
Highlight the responsibility of every staff member.
Let all staff know how to report concerns or suspicions.
3: Starters and leavers process
Identify the specific data, devices, and access privileges new starters need.
Adopt a controlled exit policy for leavers, including group password resetting.
Review returned devices, wipe or securely destroy data where necessary.
4: Maintenance, upgrades, and planning
Back up your data regularly.
Scan network and devices frequently for necessary upgrades and/or action any security updates from trusted software providers as they pop up on your computer (for example AVG Driver Updater).
Force password changes regularly.
Create an Emergency Response Plan in case of theft, breach, or loss.
Many businesses decide to invest in cybersecurity solutions offered by companies such as AVG Antivirus Subscription Business who provides all-in-one protection including firewalls, server security, and email protection backed up with technical support. Compare the AVG Business options here.
Suspecting a breach
As the statistics at the top of this page show, SMBs often aren’t immediately aware when a breach has occurred. Here are some warning signs to look out for:
Your network performance decreases suddenly and dramatically.
You can’t perform routine updates.
Your AVG antivirus Subscription software is disabled and you can’t re-enable it.
You are locked out of accounts.
The longer a breach goes undetected, the more information the criminals can steal and the more damage they can inflict. You must act fast to:
Confirm if your network has been compromised.
Contain the damage as much as possible.
Under GDPR, organisations operating in Europe must report a personal data breach to the relevant authority within 72 hours.
If the incident concerns data held on a mobile device, you may need to consider whether you can (or should) wipe or disable the device remotely. A step such as this might provoke staff disapproval - especially if the device is the property of an employee. If you’re unable to provide a separate work phone, writing a Bring Your Own Device (BYOD) policy is always recommended.
If you do have a BYOD policy, it should include a backup schedule to ensure your business data and your employees’ personal data (photos, contacts, etc) is protected. Read our article: Tips on implementing a Bring Your Own Device policy.
Once the mobile device is wiped, if you do have a backup, you can restore this after the data breach is resolved. And while a simple backup might not be the ideal solution, it will go some way to putting you back in the position you were in prior to the breach or theft. Don’t underestimate its importance.
Key action points for preventing a data breach at your small business:
Make sure you understand the confidentiality, integrity and availability of your business data.
Assess the infrastructure of your network - devices, cloud locations, etc - and who has access.
Take relevant security measures: ensure you have up-to-date AVG Antivirus Subscription for small businesses, redesign your security policies and protocols and train your staff.
Know the signs of a breach - dramatic changes in network performance, can’t perform routine updates, you are locked out of accounts, etc - so that you can confirm and report it as soon as possible.
No comments:
Post a Comment